- US | UK | INDIA | Cloud Patented Service Provider
VTM Scan
A Proactive Vulnerability Assessment Tool Protecting Your Website And Web Assets
Why VTM Scan
Protecting The Digital Identity Of Your Businesses

Standard Scan Plans
Domains: 2 Domains
Total No. of Scans: 4
Annual Cost: ₹349 249
Bulk Buy ( No. of Scans X 12): ₹3499 2499
Enterprise Scan Plan
Domains: 2 Domains
Total No. of Scans: 4
Annual Cost: ₹499 379
Bulk Buy ( No. of Scans X 12): ₹4999 3749
Standard Scan Plans
Domains: 4 Domains
Total No. of Scans: 8
Annual Cost: ₹599 449
Bulk Buy ( No. of Scans X 12): ₹5999 4449
Enterprise Scan Plan
Domains: 4 Domains
Total No. of Scans: 8
Annual Cost: ₹949 689
Bulk Buy ( No. of Scans X 12): ₹4499 6889
Standard Scan Plans
Domains: 10 Domains
Total No. of Scans: 20
Annual Cost: ₹1199 879
Bulk Buy ( No. of Scans X 12): ₹11699 8779
Enterprise Scan Plan
Domains: 10 Domains
Total No. of Scans: 20
Annual Cost: ₹1669 1249
Bulk Buy ( No. of Scans X 12): ₹16669 12499
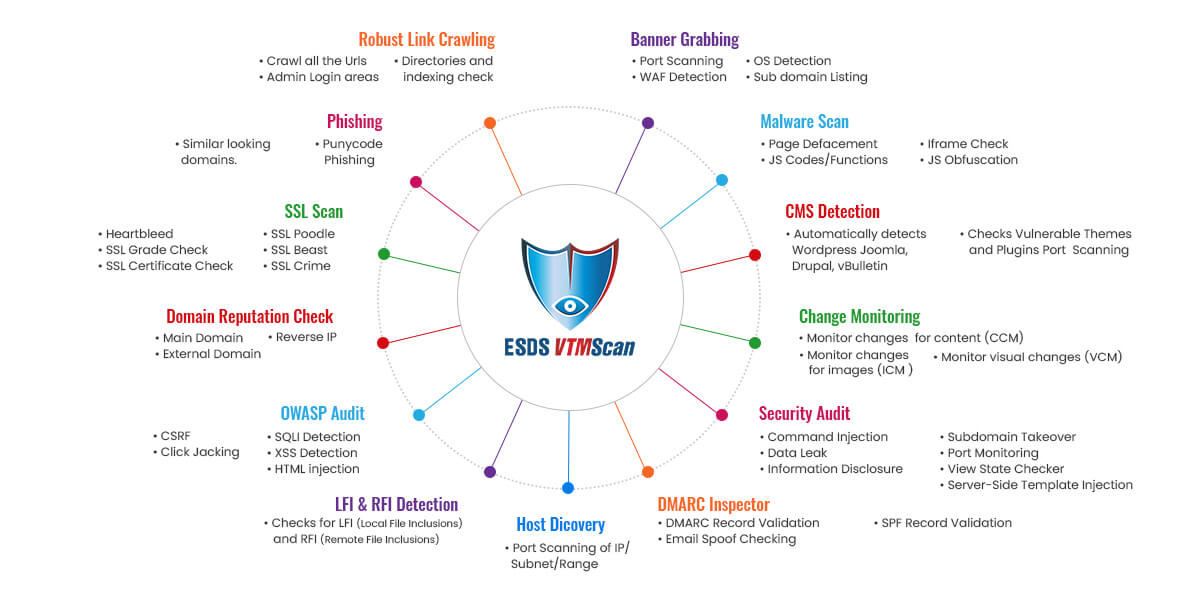
Every few years, the Open Web Application Security Project (OWASP) publishes a list of the top 10 vulnerabilities in the field of web application security. ESDS VTMScan identifies these flaws and respects the OWASP guidelines. We search for vulnerabilities such as Cross-Site Scripting (XSS), SQL Injection, Insecure Deserialization, and Sensitive Data Exposure, and report them along with advice for how to resolve them.


Content Change Monitoring is an important feature provided by ESDS VTM Scan. We scan each and every page of the ESDS VTM Scan has a useful tool called Content Change Monitoring. To identify any changes, we scan each and every page of the website. Every modification is tracked across the website, along with its proportion and associated URLs. We start by taking a snapshot of all the web pages, then check each one for modifications and report any abnormalities we find. This tool allows website owners to see if modifications are being made to their website without their knowledge or if the changes are fraudulent.
Website defacement check: Website defacement is an attack on a website that changes the visual appearance of the site or a webpage.
- Forceful redirect injection test.
- Scans JavaScript code snippets against generic signatures: Checks for JavaScript’s deprecated and vulnerable functions like eval, base64_decode, char etc. Checks for iframes.
- A special algorithm developed to detect JavaScript Obfuscation: Obfuscation used to convert vulnerable codes into an unreadable format.
- Third-party link checks: It checks third party links with reputation databases.
- Malware Monitoring primarily focuses on the detection of- JavaScript, iframe & Defaced keywords. JavaScript is scanned for malicious code. The site is also scanned for deface keywords like- ‘hacked by’, ‘compromised’, etc.


Protect your customers and safeguard your website and web application with ESDS VTMScan.
- Find similar looking domains.
- URL hijacking - The URL hijacking can be similar to the victim’s website address (e.g. esds.co.in): and also it may be of the following types -
- A common misspelling, or foreign language spelling. Eg- site: eads.com
- Misspelling like a typographical error. Eg - site: essd.com
- Swapping letters within the name Eg- site: essd.com
- Different domain name. Eg - site: esds.org
- Corporate intelligence.
- Homoglyph advance phishing attack detection.
- Punycode phishing attack detection.
Protect your customers and safeguard your website and web application with ESDS VTMScan.
- Very few scanners provide this feature.
- Detect Wordpress, Joomla, vBulletin, Drupal.
- Scan Themes, Plug-ins, unprotected admin area.
- User enumeration.
- Brut forcing for simple password detection.
- FPD - File Path Disclosure scanning.
- Detect CMS in all directories.


Domain reputation in Google, SURBL, Malware Patrol, Clean-Mx, Phishtank,Sorbs, Spamcop, Abusech, Isc.
Google, SURBL, Malware Patrol, Clean MX, PhishTank, Sorbs, Spamco p,Abusech,Isc - ESDS VTMScan analyses if your domain is listed in these databases. These companies have databases that contain IP addresses and domains that are used to extract data for malware, spamming, and phishing.
IP addresses on RBLs (Real-time Blackhole Lists) are those whose owners refuse to stop spam from spreading. RBL compiles a list of server IP addresses from a variety of ISPs (Internet Service Providers) whose customers are spammers. RBL also keeps track of ISPs whose servers have been used to transmit spam. The mail server IPs in 58 such RBL repositories were checked using ESDS VTMScan.


Link crawling is the process of collecting all of the website's websites (URLs). It assists us in determining how many websites our website has and what these pages are about. The website owner can also double-check whether or not these pages are genuine.
- Crawls links from web pages, robots.txt, iframes, hacker’s favourite search engines, directory indexes, and directory traversals.
- Check admin and directory busters.
- Directory access check.
ESDS VTMScan checks for SSL Poodle, BEAST, CRIME, Heartbleed, DROWN,SSL grade check,SSL Certificate check etc.
In SSL Check, the following areas are checked:
- NULL Cipher used or less than 128 bits.
- Domain uses an invalid security certificate.
- Domain uses an expired security certificate.
- Domain uses a security certificate which expires today (EOD).


Local File Inclusion (LFI) is a method of injecting a file or script on a server via a web browser, allowing local directory traversals and characters to be injected if the page is not sanitised. Sensitive information is exposed as a result of this attack.
Remote File Inclusion (RFI):Remote File Inclusion (RFI) is an attack that looks for vulnerabilities in a web application and uses a script on the web browser to include a remote file. The criminal intends to use an application's functionality to upload malware from a different domain.
Data Leak's new functionality has been released. Unauthorized data transmission from an organisation to an external destination is known as data leakage. VTMScan determines whether or not a data breach has happened and shows the results in the form of a correct list under the page source. VTMScan sends forth relevant signals like this.


ESDS VTMScan DMARC inspector validates DMARC, SPF records and check for email spoofing is possible or not.And also validates DKIM records.
- Information disclosure: VTMScan examines the URL to see if sensitive information has been published. IP addresses, emails, phone numbers, and other types of sensitive information are examples. VTMScan searches the whole site for this type of information and alerts you to it.
- View State Checker: To reduce the risk of someone interfering with the data contained in the ViewState, it's a good idea to encrypt it. The ViewState data in the target web application is not encrypted. VTMScan recognises ViewState and determines if it is strong or weakly encrypted.
- Email Spoofing Checking: Email spoofing is the act of sending emails from a fake sender address. The VTMScan email spoof checker determines whether or not emails may be faked.


How VTMScan Can be Beneficial
Contact Form
Address
UAE Office
Office no 315, 3 rd floor, DIC Building No . 10, Dubai Internet City, Dubai, UAE
